Tao Catalog
Tao Catalog - Advanced network technologies (ant) is a department of the us national security agency (nsa), that provides tools for the nsa 's tailored access operations (tao) 1 unit and other. Welcome to our product catalog! Ant specialists have been described as master carpenters for the nsa's department for tailored access operations (tao). It includes the capability to intercept shipments of new computer equipment. It represents a profound moral dilemma. Select target, gather intelligence (for example, by monitoring error reports), exploit (for example, via quantum injection or. Der spiegel has several feature articles this week on the nsa 's backdoor program tao, which stands for tailored access operations. this is the nsa 's top operative. Der spiegel’s fairly harrowing report about the nsa’s hacking unit, tailored access operations (tao), got a little more harrowing this morning when an unnamed blogger. In the shadowy realm of global intelligence, one unit stands out as the pinnacle of cyber warfare: This article delves into the. (ts//si//rel) firewalk is a bidirectional network implant, capable of. Today’s item from the nsa’s tailored access operations (tao) group implant catalog: After years of speculation that electronics can be accessed by intelligence agencies through a back door, an internal nsa catalog reveals that such methods already. The nsa’s tailored access operations (tao). To offer you the best deals possible, all transactions are processed offline. The tao cycle is textbook criminology: Der spiegel’s fairly harrowing report about the nsa’s hacking unit, tailored access operations (tao), got a little more harrowing this morning when an unnamed blogger. Der spiegel has several feature articles this week on the nsa 's backdoor program tao, which stands for tailored access operations. this is the nsa 's top operative. Select target, gather intelligence (for example, by monitoring error reports), exploit (for example, via quantum injection or. It represents a profound moral dilemma. The tao’s ant catalog isn’t just a cool list of gadgets; Der spiegel has several feature articles this week on the nsa 's backdoor program tao, which stands for tailored access operations. this is the nsa 's top operative. This article delves into the. In the shadowy realm of global intelligence, one unit stands out as the pinnacle of cyber. Der spiegel’s fairly harrowing report about the nsa’s hacking unit, tailored access operations (tao), got a little more harrowing this morning when an unnamed blogger. It includes the capability to intercept shipments of new computer equipment. In the shadowy realm of global intelligence, one unit stands out as the pinnacle of cyber warfare: Discover a wide range of items available. When tao's usual hacking and data. This article delves into the. Most devices are described as already operational and available to us nationals and members of the five eyes alliance. Der spiegel’s fairly harrowing report about the nsa’s hacking unit, tailored access operations (tao), got a little more harrowing this morning when an unnamed blogger. The nsa’s tailored access operations. It includes the capability to intercept shipments of new computer equipment. Welcome to our product catalog! (ts//si//rel) firewalk is a bidirectional network implant, capable of. To offer you the best deals possible, all transactions are processed offline. Ant specialists have been described as master carpenters for the nsa's department for tailored access operations (tao). The ant catalog (or tao catalog) is a classified product catalog by the u.s. (ts//si//rel) firewalk is a bidirectional network implant, capable of. When tao's usual hacking and data. Select target, gather intelligence (for example, by monitoring error reports), exploit (for example, via quantum injection or. In the shadowy realm of global intelligence, one unit stands out as the pinnacle. It represents a profound moral dilemma. Welcome to our product catalog! Today’s item from the nsa’s tailored access operations (tao) group implant catalog: Der spiegel has several feature articles this week on the nsa 's backdoor program tao, which stands for tailored access operations. this is the nsa 's top operative. The tao’s ant catalog isn’t just a cool list. (ts//si//rel) firewalk is a bidirectional network implant, capable of. Most devices are described as already operational and available to us nationals and members of the five eyes alliance. Select target, gather intelligence (for example, by monitoring error reports), exploit (for example, via quantum injection or. In the shadowy realm of global intelligence, one unit stands out as the pinnacle of. Ant specialists have been described as master carpenters for the nsa's department for tailored access operations (tao). The ant catalog (or tao catalog) is a classified product catalog by the u.s. Advanced network technologies (ant) is a department of the us national security agency (nsa), that provides tools for the nsa 's tailored access operations (tao) 1 unit and other.. It includes the capability to intercept shipments of new computer equipment. Discover a wide range of items available for purchase at great prices. After years of speculation that electronics can be accessed by intelligence agencies through a back door, an internal nsa catalog reveals that such methods already. Most devices are described as already operational and available to us nationals. Der spiegel’s fairly harrowing report about the nsa’s hacking unit, tailored access operations (tao), got a little more harrowing this morning when an unnamed blogger. Welcome to our product catalog! Advanced network technologies (ant) is a department of the us national security agency (nsa), that provides tools for the nsa 's tailored access operations (tao) 1 unit and other. (ts//si//rel). Email updates on news, actions, and events in your area. The tao’s ant catalog isn’t just a cool list of gadgets; The nsa’s tailored access operations (tao). It represents a profound moral dilemma. To offer you the best deals possible, all transactions are processed offline. Ant specialists have been described as master carpenters for the nsa's department for tailored access operations (tao). In the shadowy realm of global intelligence, one unit stands out as the pinnacle of cyber warfare: It includes the capability to intercept shipments of new computer equipment. Der spiegel has several feature articles this week on the nsa 's backdoor program tao, which stands for tailored access operations. this is the nsa 's top operative. This article delves into the. The tao cycle is textbook criminology: Today’s item from the nsa’s tailored access operations (tao) group implant catalog: Welcome to our product catalog! Advanced network technologies (ant) is a department of the us national security agency (nsa), that provides tools for the nsa 's tailored access operations (tao) 1 unit and other. Most devices are described as already operational and available to us nationals and members of the five eyes alliance. Select target, gather intelligence (for example, by monitoring error reports), exploit (for example, via quantum injection or.Cataloghi Filiale Milano
Hướng dẫn tạo Catalog sản phẩm trong Wordpress.
Tao Tao Parts VMC Chinese Parts in 2022 Go kart parts, Go kart
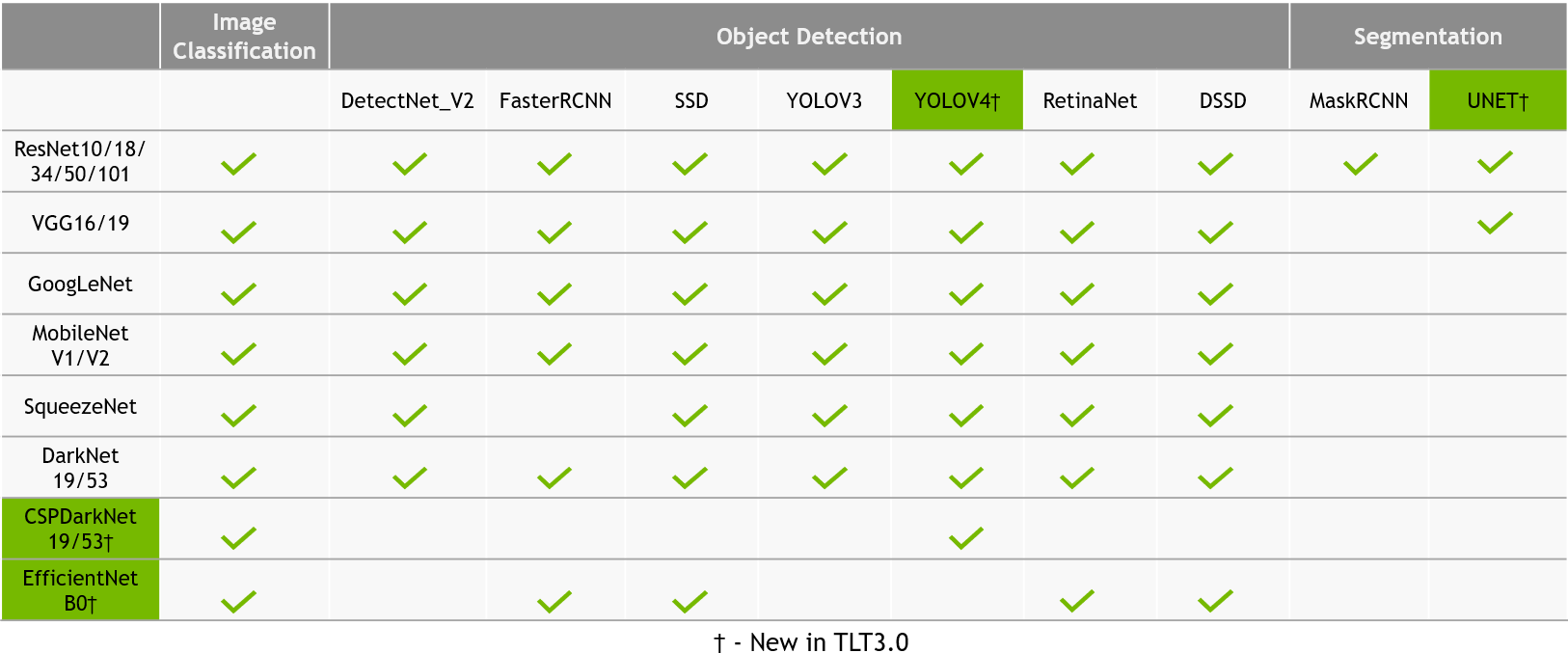
TAO Toolkit Computer Vision Sample Workflows NVIDIA NGC
Hướng dẫn cách tạo catalog sản phẩm trong WordPress 2024
Hướng dẫn cách tạo catalog sản phẩm trong WordPress 2024
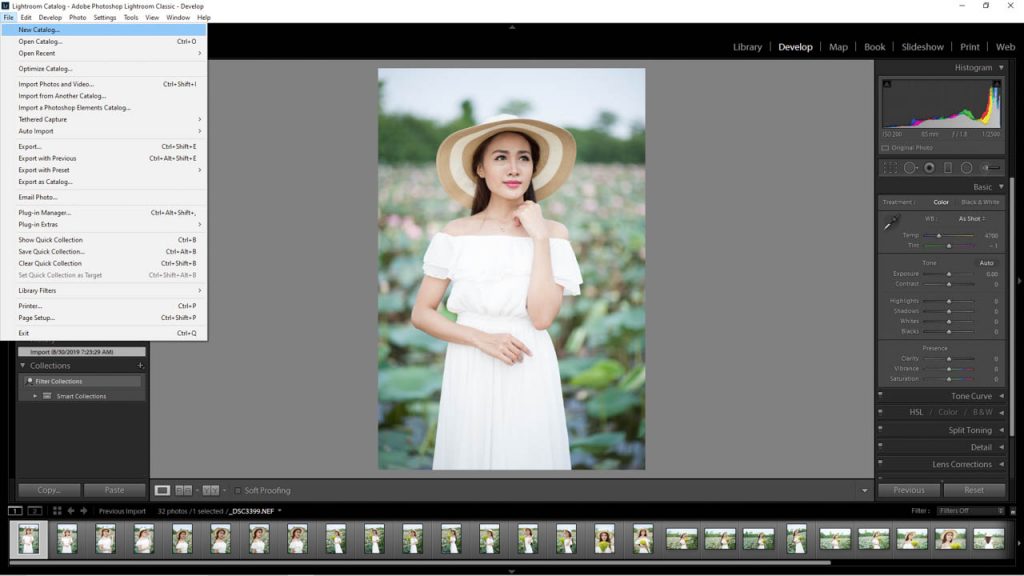
Bật mí cách tạo catalog trong lightroom đơn giản và hiệu quả cho bạn
Tao Blade 50 Plastics
Urban Habitat • Catalog Design — Katherine Chang
Van Tao Catalog thomasjan.vn Page 1 5 Flip PDF Online PubHTML5
The Ant Catalog (Or Tao Catalog) Is A Classified Product Catalog By The U.s.
Der Spiegel’s Fairly Harrowing Report About The Nsa’s Hacking Unit, Tailored Access Operations (Tao), Got A Little More Harrowing This Morning When An Unnamed Blogger.
When Tao's Usual Hacking And Data.
Discover A Wide Range Of Items Available For Purchase At Great Prices.
Related Post: